The blockchain ecosystem is currently facing an alarming security threat, as a shocking wallet draining operation has been stealthily targeting crypto-native individuals for months. The attacker, still unidentified, has siphoned off more than 5,000 ETH and a plethora of tokens, NFTs, and coins across 11 different chains since December 2022. This large-scale operation has left the crypto community on high alert, as it raises crucial concerns about blockchain security and Bitcoin safety in the rapidly evolving digital landscape.
Who Is at Risk of Wallet Draining?
The wallet draining operation targets seasoned crypto users, also known as “OGs”, who tend to have multiple addresses and work within the crypto space. If you’re reading this article, chances are, you might be at risk of falling victim to this operation.

Redefining Scams: The Wallet Draining Menace
This wallet draining operation stands out from the usual low-brow phishing sites or random scammers that often target unsuspecting newcomers in the crypto space. The sophisticated attacker behind this operation has been specifically targeting seasoned crypto users, demonstrating a high level of expertise and knowledge in the field. This level of precision and planning emphasizes the gravity of the situation and serves as a warning to all crypto holders to prioritize the security of their digital assets.
Mysterious Commonalities
Despite thorough forensic analysis on multiple devices, no one has determined the source of the compromise. The only known commonalities among the victims are:
- Keys created between 2014-2022
- Crypto-native individuals with multiple addresses and involvement in the industry
The Attacker’s Distinctive Wallet Draining Methods
The sophisticated attacker behind the wallet draining operation employs highly distinctive methods in both their theft and post-theft on-chain activities. These well-defined patterns provide valuable insights into the attacker’s tactics and strategies, offering potential leads to their identification and prevention of future attacks.
Carefully Timed Wallet Draining Operations
The attacker meticulously plans and executes their operations within specific timeframes. Primary theft transactions predominantly occur between 10 am – 4 pm UTC, while secondary thefts and “dust” collection typically take place between 4 pm – 10 pm UTC. This careful timing suggests the attacker may be operating within a particular timezone or working schedule, possibly narrowing down their location.
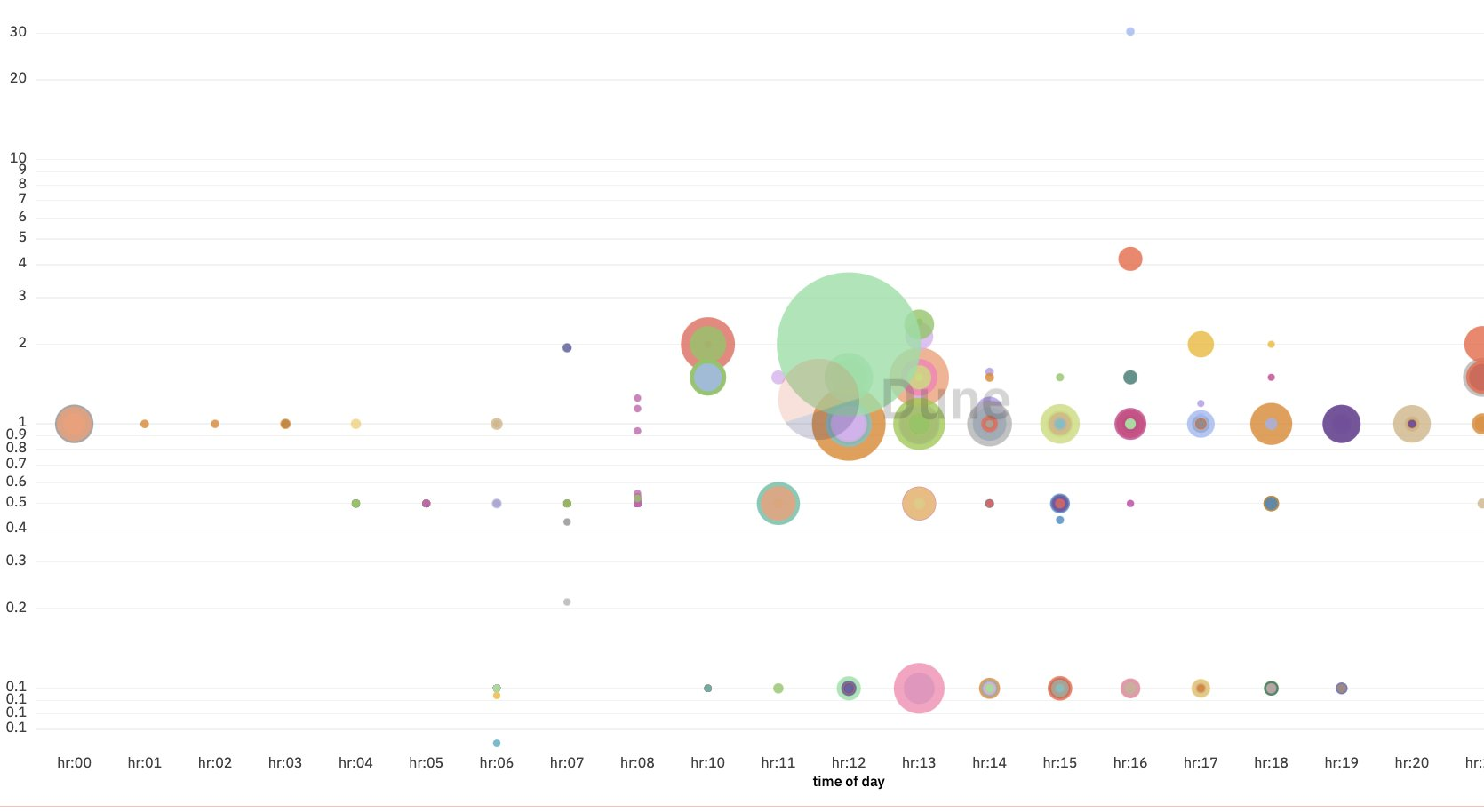
Image credit: @tayvano_
Asset Conversion and Movement
The attacker demonstrates an impressive knowledge of the crypto landscape, converting tokens to ETH within the victim’s wallet using platforms like MetaMask Swaps, Uniswap, or 0x. By doing so, they can efficiently transfer the stolen assets while minimizing transaction fees and traces. Their familiarity with the inner workings of these platforms highlights their expertise in the field, making them even more elusive.
Targeting Vulnerabilities and Oversights
A key aspect of the attacker’s method is exploiting the vulnerabilities and oversights of their victims. They often miss staked positions, NFTs, or lesser-known tokens during the initial sweep, only to return hours, days, or even months later to collect the remaining assets. This tactic showcases their persistence and relentless pursuit of maximizing the gains from each victim.
Complex Chain of Wallet Draining Victims
The attacker frequently moves assets between multiple victims’ addresses or even across different blockchains, creating a complex chain of transactions that makes it difficult to track their activities. This elaborate strategy not only obscures their identity but also implicates other victims as part of the operation, further complicating investigations.
Mastery of Anonymity Techniques
The attacker leverages a variety of anonymity techniques to maintain their secrecy. They use centralized swappers, such as FixedFloat, SimpleSwap, and ChangeNOW, to move the stolen assets and ultimately convert them to Bitcoin. Once the assets are consolidated in a few Bitcoin addresses, the attacker uses mixing services like Coinomize, Wasabi, or CryptoMixer to further obfuscate the funds’ origins, making it incredibly challenging to trace their activities.
How to Stay Safe and Prevent Wallet Draining?
The attacker is not targeting any specific wallet or exploit. The best course of action is to:
- Don’t keep all your assets in a single key or secret phrase for years.
- Split up your assets and migrate them to properly secured wallet.
- Regularly update your wallet’s security measures and follow best practices for safeguarding your private keys.
- Keep an eye on your assets and monitor any unusual activity in your wallet. If you notice suspicious transactions, take immediate action to secure your assets.
- Be cautious about sharing sensitive information related to your wallet or private keys online.
- Consider diversifying your investments across multiple wallets or platforms to minimize the risk of losing all your assets in a single attack.
- Stay informed about the latest security threats in the crypto space and adopt preventive measures to protect your assets.
Identifying the Wallet Draining Attacker
The attacker’s identity remains unknown, and the source of the exploit is unidentified. Recent IPs associated with the attacks involve a mix of VPNs, proxies, and other services, making it difficult to pinpoint a single source.
The attacker seems to have used various devices and operating systems, including Windows/Chrome, Windows/Firefox, and Mac/Chrome, further complicating the investigation.
Interestingly, many of the thefts seem to take place on weekends, although it’s unclear why this pattern has emerged. Crypto community collaboration and information sharing are essential for identifying the attacker and preventing further losses.
Staying Secure in the Evolving Blockchain Landscape
The massive wallet draining operation serves as a crucial wake-up call, emphasizing that even seasoned crypto users can fall prey to advanced and targeted attacks. In the ever-evolving blockchain landscape of 2023, it has become increasingly important to prioritize the security of digital assets and remain up-to-date with the latest threats.
As blockchain technology advances and the number of users and assets in the crypto space continues to grow, so does the appeal for cybercriminals. With the increasing complexity of blockchain ecosystems, new vulnerabilities and attack vectors are bound to emerge. Consequently, it is essential to adopt a proactive approach to secure your digital assets.
To maintain a high level of security in this fast-paced environment, consider the following strategies:
- Educate yourself about the latest security threats and best practices within the blockchain and crypto industry. Participate in security webinars, read articles, and engage in community discussions to stay informed.
- Regularly assess and update your security measures. This may include using multi-signature wallets, biometric authentication, and robust password management practices.
- Utilize a multi-layered security approach by employing firewalls, intrusion detection systems, and secure network protocols to safeguard your assets and transactions.
- Monitor advancements in blockchain security solutions, such as zero-knowledge proofs, secure multi-party computation, and privacy-enhancing technologies, to better protect your assets and identity.
- Collaborate with the crypto community to share information, raise awareness, and collectively improve the security of the entire ecosystem.
The wallet draining operation underscores the importance of staying vigilant and adopting best practices to protect your digital assets. By staying informed and proactive, you can minimize the risk of falling victim to sophisticated attacks and help others in the crypto community stay safe as well.
Source: https://twitter.com/tayvano_/status/1648187031468781568